SMiShing
Humans are said to be the weakest link in the cybersecurity chain and could be easily targeted using social engineering attacks, such as phishing. Phishing can be defined as a fraudulent attempt made by hackers to lure a person into divulging their sensitive information, such as username, password, credit/debit card details, etc.
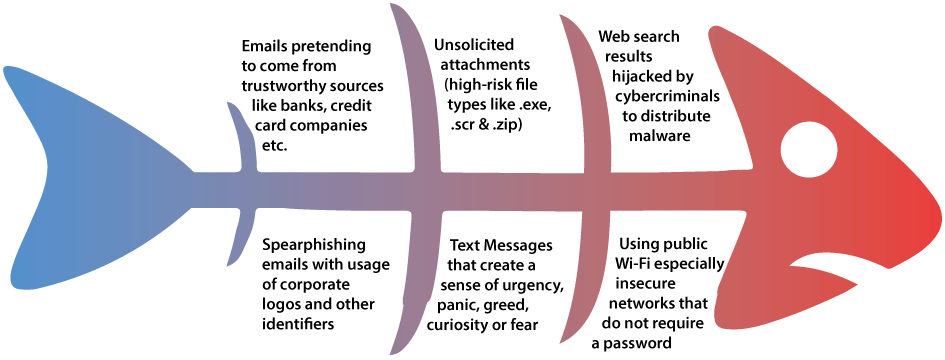
Phishing shows no sign of slowing down anytime soon and will only continue to evolve in sophistication and effectiveness. It is currently one of the most popular modes of delivery for malware infections whether to steal sensitive information or gain a foothold into the network of an organization. An organization that has fallen victim to a successful phishing attack will often sustain huge financial losses, in addition to the loss of customer’s trust and reputational damage.
What Is SMiShing?
SMiShing, also known as SMS Phishing, could be classified as a type of social engineering attack. Unlike email phishing, which uses emails to carry out attacks, SMiShing is done through text messages. A typical example of SMiShing is when a threat actor impersonates a legitimate entity such as your organization’s IT service/security admin, banks, government agency, e-commerce, package delivery, etc., to trick their victims into divulging their username/passwords or other sensitive information.
Although there has been an increase in awareness surrounding SMiShing scams, the threat posed by SMiShing scams cannot be ignored because the majority of us still depend on SMS and other similar mobile applications to communicate with one another. A survey has shown that in 2019, 60% of SMS users received spam messages once a week, and 28% almost every day.
What makes SMiShing scarier is that many of us tend to trust SMS messages more than email messages. The way SMiShing works is similar to that of phishing, wherein an attacker pretends to be from your bank and asks for your details or encourages you to click/visit a link to get an offer, reward, or a discount. This action will enable the threat actor to obtain your sensitive data or initiate a malware download process in the background.
The year 2019 has seen a sharp rise in phishing activities, where nearly 71% of phishing attacks were financially motivated, as reported by security experts. Nearly 29% of breaches involved the use of stolen credentials, and nearly 33% of breaches used social engineering. As opposed to the general assumption that large organizations are frequently targeted by phishing attacks, nearly 43% of breaches involve small-scale businesses and industries.
Why Is It Important to Secure a Mobile Device Against SMiShing?
- There are 5 billion smartphone users worldwide.
- Two-thirds of internet users use shopping apps on their mobile devices.
- Six out of ten shoppers say the possibility to shop via mobile devices is an important factor in brand selection.
- Mobile web traffic accounts for 52.6% of global web traffic.
- More than two-thirds of the total digital ad spend in 2019 was on mobile ads.
- The global retail conversion rate on mobile phones is 1.82%, compared to 3.9% for desktops.
These statistics show that a large number of people use a mobile device for personal and official purposes. Thus, any random mobile device has a high probability of containing sensitive data, such as financial & security information, username/password, etc. which could easily be exfiltrated by hackers if they are able to successfully install spyware or other malware onto the device.
How to Defend Against SMS Phishing
Defending against SMiShing attacks begins with providing simulations and awareness trainings to your organization’s employees in order to increase their security awareness surrounding such issues. To help achieve this, Aware’s SMiShing simulations are designed to test your employees in the same way a cybercriminal would and improve their understanding of the dangers associated with this threat.
SMiShing Templates
We can help you to establish a baseline measurement on how susceptible your employees are to SMiShing attacks and measure their progress against the baseline.
Design Your Campaign
We can help you schedule your campaigns accordingly in order to maximize the visibility of your campaigns.
Providing Training
We provide simulation reports and training materials to help improve the security awareness of your employees
Prominent Features of Aware
Along with testing and training, Aware also offers additional features based on your requirements, such as the scale of operations, campaign statistics, etc.
- Learning Management (LMS Integrations)
- Learning Management System with Autoenroll
- Priority Level Support
- Support Resources and Email Support
- Email and Phone Support
- Dedicated Consultant Support
- Customer Support
- Active Directory Support
- Multiple Language Support
- Real-Time Visible Training Results
- Campaigns Summary
- Unified Dashboard
- Advanced Reporting
- Reporting APIs
- Branded Reports
- Print & Export Reports
- Basic Reporting
- Reporting and Analytics
- Board of Directors Report
- Editable Executive Report (Word doc)
- Preset Template Library
- Customizable Template Library
- Template Creation
- Professional Template Services
- Active Phishing Threat Templates
- Education Templates
- Multiple Template Campaigns
- Schedule Real-Time Email Alerts for Campaigns
- Automated Training Campaigns
- Outlook Plugin to Report Suspicious Email
- Advanced API Integration
- Mail Server/LDAP Integration
- Active Directory Integration
- Office 365 Integration
- Exchange On-Premises Integration
- Outlook & Office Integration
- OWA Plugin
- Google Apps Integration
- Gmail Plugin
- Mobile Integration
- Priority Level Support
- Support Resources and Email Support
- Email and Phone Support
- Dedicated Consultant Support
- Customer Support
- Active Directory Support
- Multiple Language Support
- Unlimited Phishing Simulations
- Schedule Features
- Website Cloning Tool
- Industry Benchmarking
- Vishing Security Test
- SMS/Text Phishing Simulations
- Smart Groups
- Security Roles
- USB Drive Test
- Educational Content Library
- Administrative Features
- MSP Account Management
- Professional Services
- CBT Modules
- Advanced Theme Selector
- Automated Playbooks
- Advanced Analytics
- Mobile Responsive Modules
- Credentials - Data Entry
- Password Capture
- Attachments in Phishing Template
- Pre-Launch Test
- Preset Landing Page Templates
- Customizable Landing Pages
- Reporting KPIs
- Click Rate
- Opened Messages
- No Response
- Campaign History
- Repeat Offenders
- Deployment
- On-Prem
- SaaS
- Hybrid
How Often or Long Should a SMiShing Campaign Be Carried Out?
Studies have reported phishing to be responsible for a loss of $26 billion between 2016 to 2019, and this is expected to grow in 2020. SMishing simulations and trainings are not a one-time activity, they need to be carried out regularly to ensure optimal retention and effective learning. As cybercriminals continue to ramp up their game, organizations must ensure that their employees are equipped to defend their organizations against phishing attacks. How often or how long a company must adopt and incorporate anti-phishing solutions depend on factors such as:
- The scale of operations.
- Compliance with various regulatory laws.
- The existing security infrastructure.
- Threat identification & management capability of the employee/user.